Balbharati Maharashtra State Board Class 11 Information Technology Solutions Chapter 4 Cyber Law Textbook Exercise Questions and Answers.
Maharashtra State Board Class 11 Information Technology Solutions Chapter 4 Cyber Law
1. Complete the following web.
Question 1.
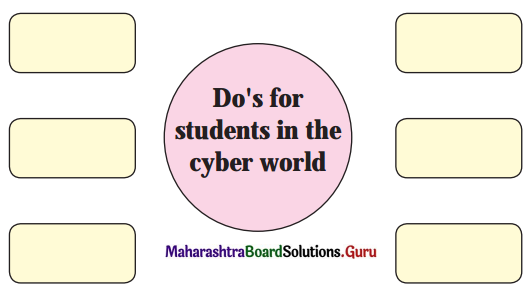
Answer:
- Use the Internet for the knowledge base.
- Use the Internet to communicate messages.
- Respect the privacy of other users on the Internet.
- Download legitimate and authentic programs from the Internet.
- Use licensed software on your computer.
- Check to see if the web address begins with https:// whenever you sign in.
- Report and flag content that is abusive or illegal.
![]()
2. Complete the following chart.
Question 1.
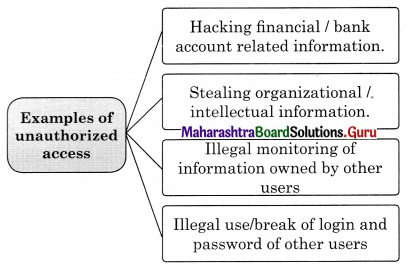
Answer:
3. Fill the following boxes with the appropriate cybercrime name.
Question 1.
Copyright violation of software created originally by an individual.

Answer:
Software Piracy
Question 2.
Gaining access without the user’s permission.

Answer:
Unauthorized Access
![]()
Question 3.
Extracting confidential information by email.
Answer:
Phishing
4. Read the following and answer the question.
Rahul lost his pen drive in his college computer lab. His classmate Madhav finds it. He carries it home to return it to him the next day. When Madhav opens it he finds his favourite game. He thinks of making a duplicate copy of the game software.
Question I.
Does Madhav think ethically?
Answer:
No
Question II.
What do you think should Madhav do?
Answer:
Madhav should return back the pen drive. He has done unauthorized access.
Question III.
If he makes a duplicate copy then which cybercrime will he commit?
Answer:
Software Piracy
5. Answer in brief.
Question 1.
What care should be taken by the user while doing online activities?
Answer:
- Stick to copyright restrictions when downloading anything from the internet.
- Use strong passwords with combinations of numbers. Uppercase and lowercase letters and special characters.
- Always scan files before opening them.
- Don’t talk to strangers.
- Think before posting something on social media related to any sensitive topic like politics, religion, etc.
- Report to the service provider if the account is hacked; if possible deactivate your account.
- Whenever you sign in online check if the web address begins with https: //
Question 2.
Define the terms (1) Ethics (2) Moral
Answer:
Ethics:
Ethics also called moral philosophy is the discipline concerned with what is morally good and bad, right or wrong.
Moral:
The standards of behaviour; principles of right and wrong behaviour. Thus morals are dictated by society, culture, or religion while ethics are chosen by the person himself which governs his life.
![]()
Question 3.
Explain three examples related to unauthorized access?
Answer:
- Hacking financial/bank account-related information.
- Stealing organizational/intellectual information.
- Illegal monitoring of information owned by other users.
- Illegal use/break of login and password of other users.
- Causing intentional irritation to other users by means of damaging software and important information.
Question 4.
Explain software piracy and Hacking.
Answer:
Software piracy:
Software piracy is the illegal copying, distribution, or use of the software. It 15 such a profitable “business” that it has caught the attention of organized crime groups in a number of countries. According to the Business Software Alliance (BSA), about 36% of all software in current use is stolen.
Hacking:
Hacking refers to unauthorized intrusion into a computer or a network. Hacker is a person intensely interested in the deep and hidden or concealed working of any computer operating system and programming language. They might discover loopholes within systems and reasons for such loopholes.
6. State true or false.
Question 1.
A firewall is used to encrypt the transmission of data.
Answer:
True
Question 2.
The standards of behaviour; the principle of right or wrong are referred to as moral.
Answer:
True
![]()
Question 3.
Hacking bank account-related information is an example of software piracy.
Answer:
False
Question 4.
Phishing is representing someone else’s work as own without permission.
Answer:
True
7. Match the following.
Question 1.
| (A) | (B) |
| (1) Copying a game file | (a) Firewall |
| (2) Law related to internet | (b) Cyberthreat |
| (3) Network security | (c) Software piracy |
| (4) System crashes suddenly | (d) Cyber Law |
Answer:
| (A) | (B) |
| (1) Copying a game file | (c) Software piracy |
| (2) Law related to internet | (d) Cyber Law |
| (3) Network security | (a) Firewall |
| (4) System crashes suddenly | (b) Cyberthreat |
8. Observe the following picture and give your opinion about it by responding to the following questions.
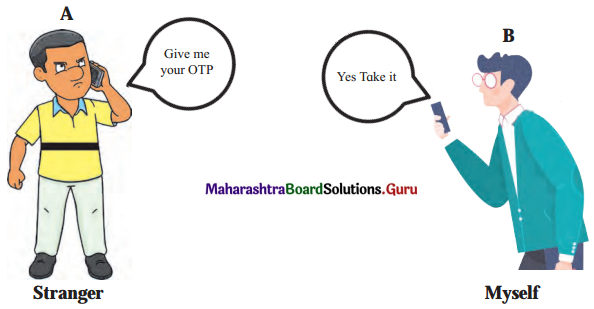
Question 1.
Is ‘B’s response correct or not?
Answer:
No B’s response is not correct.
![]()
Question 2.
What will be the consequences of ‘B’s reply?
Answer:
With all such crucial information like OTP in hand, the fraudster can easily carry out illegal financial transactions using B’s identity.
Question 3.
Which type of cybercrime does the picture depict?
Answer:
Fake Call Frauds